- Imam, Hussein e gli altri predicatori erranti: la via dei Balcani per colpire l’Italia
- Counter-terrorism in Italy: prevention and control over the territory
- The distribution platforms of ISIS propaganda - UGC, websites, file hosting
- AQ 9/11 Anniversary Message
- 20,000 ISIS military uniforms seized in Spain
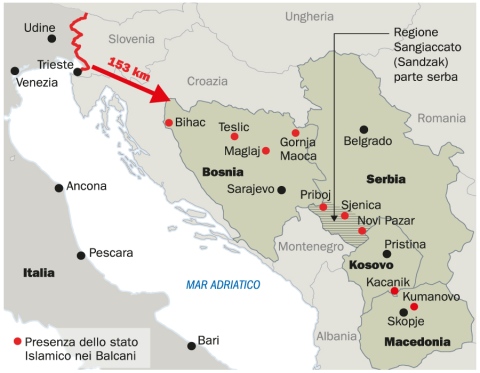
Imam, Hussein e gli altri predicatori erranti: la via dei Balcani per colpire l’Italia
Articolo di Gabriele Moroni, pubblicato oggi su Il Giorno. È il 2012 e la mappa aggiornata dell’Antiterrorismo copre l’intera penisola per dedicare una preoccupata riflessione alle strutture di culto “clandestine”, non ufficiali, e a quelle spacciate per associazioni para-culturali. Sarebbero circa 200, dalla Valle d’Aosta alla Sicilia le strutture “ombra” dove si farebbe del proselitismo, di cui 12 tenute sotto osservazione a Napoli. La base dell’indottrinamento rimane al Nord, con circa 45 fra soggetti e ritrovi…
Read More