- Imam, Hussein e gli altri predicatori erranti: la via dei Balcani per colpire l’Italia
- Counter-terrorism in Italy: prevention and control over the territory
- The distribution platforms of ISIS propaganda - UGC, websites, file hosting
- AQ 9/11 Anniversary Message
- 20,000 ISIS military uniforms seized in Spain
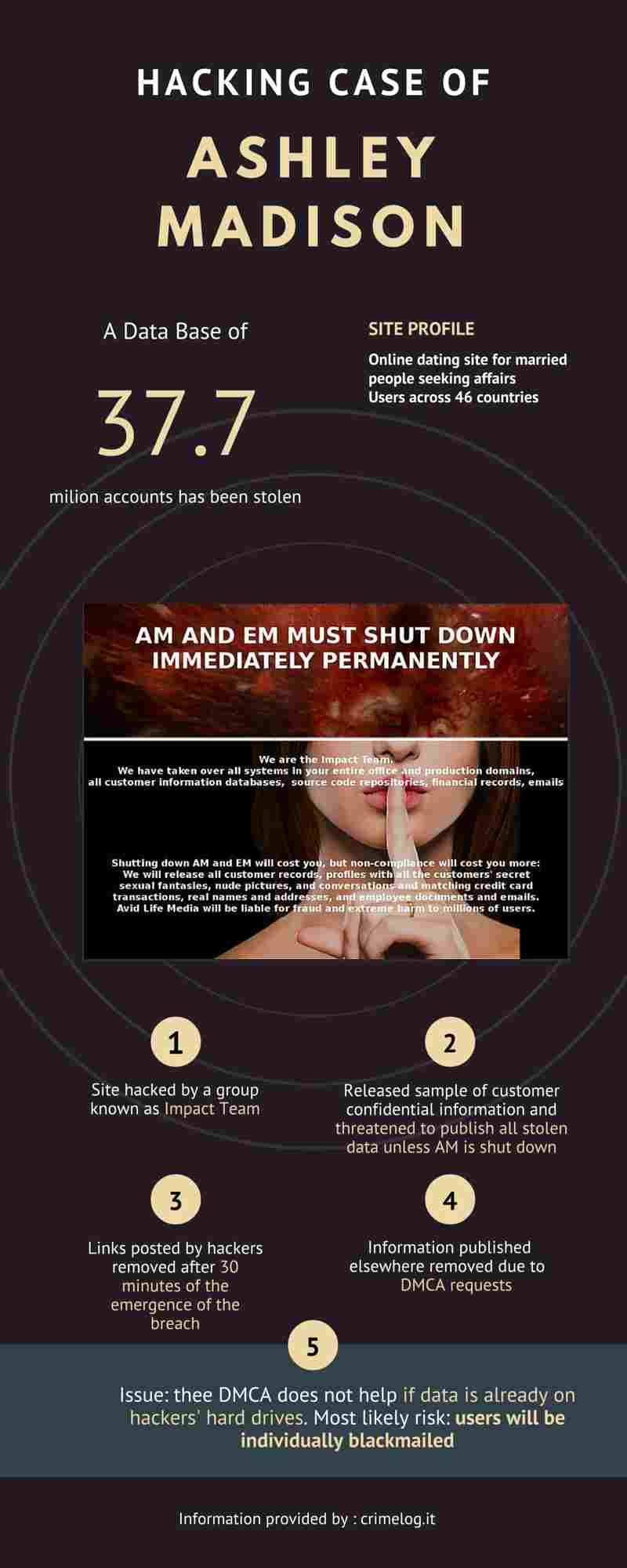
The Ashley Madison case

Some days ago, Forbes published an article of Jason Bloomberg (http://www.forbes.com/sites/jasonbloomberg/2015/07/23/ashley-madison-extortion-attack-critical-lessons-for-enterprise-cybersecurity/3/) highlighting some important lessons learned from this case.
- All the organizations are vulnerable to attack, but also “they have already been attacked”. So the real question to pose “is not when the attack might occur, but how long hackers have been inside a network and how best to mitigate further damage”.
- “Hackers are usually thieves, looking for financial gain. Some times they are vandals, intent on destruction. But what if they are extorsionists, looking to shut down your organization entirely?”.
- “You must protect all sensitive information. Organizations already know to protect personal information of customers and employees, intellectual property secrets, passwords, private keys, and the like. But an extortionist will be seeking confidential information that simply has the power to embarrass your organization, regardless of any potential financial value”.
His call on risk of hacks for ransom sounds then fine, particularly when, as in this case, the hackers’ motivation does not seem to be a finacial gain or a political agenda, but “moral outrage”.